2023 Annual Cybersecurity Attitudes and Behaviors Report

In an online-centric world, almost 90% of data breaches stem from human error. The latest report underlines the widespread digital presence and security challenges, noting that while most find cybersecurity crucial, many feel overwhelmed. Training and best practices, like using unique passwords and multi-factor authentication, are urged to combat cybercrimes, which have affected over a quarter of respondents.
How to Access SharePoint as an External User
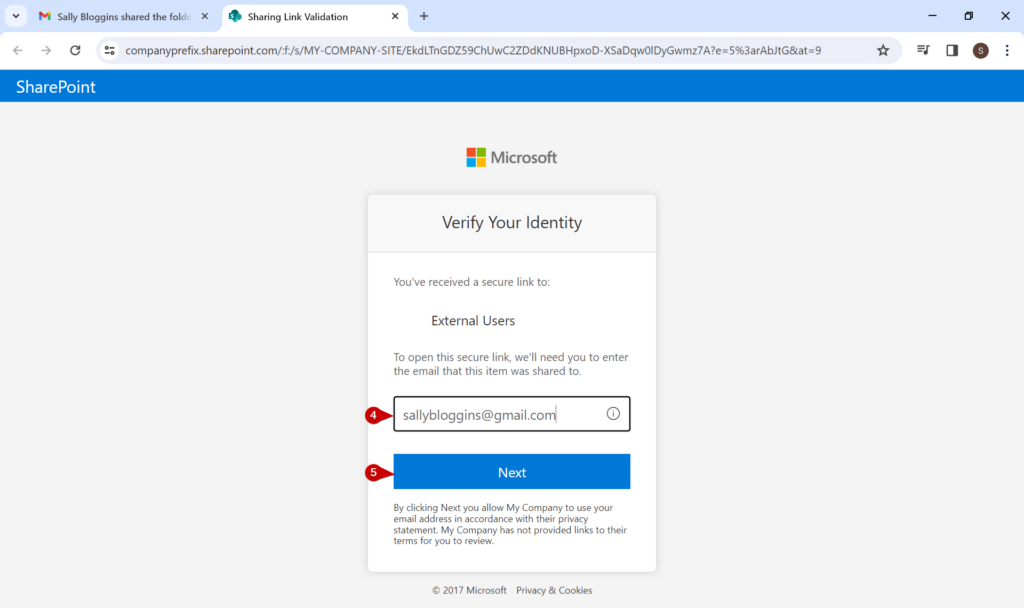
This article explains how to access a company’s SharePoint resources from a link they have shared with you via email.
Be Careful When Scanning QR Codes

QR codes, handy for quick access to content, have a dark side with scammers using them for phishing. Fake codes may steal data, install malware, or trick you into payments. Stay vigilant: verify sources, inspect URLs before clicking, and keep devices updated. Contact us for anti-phishing solutions.
How to Share Files and Folders in SharePoint with External Users
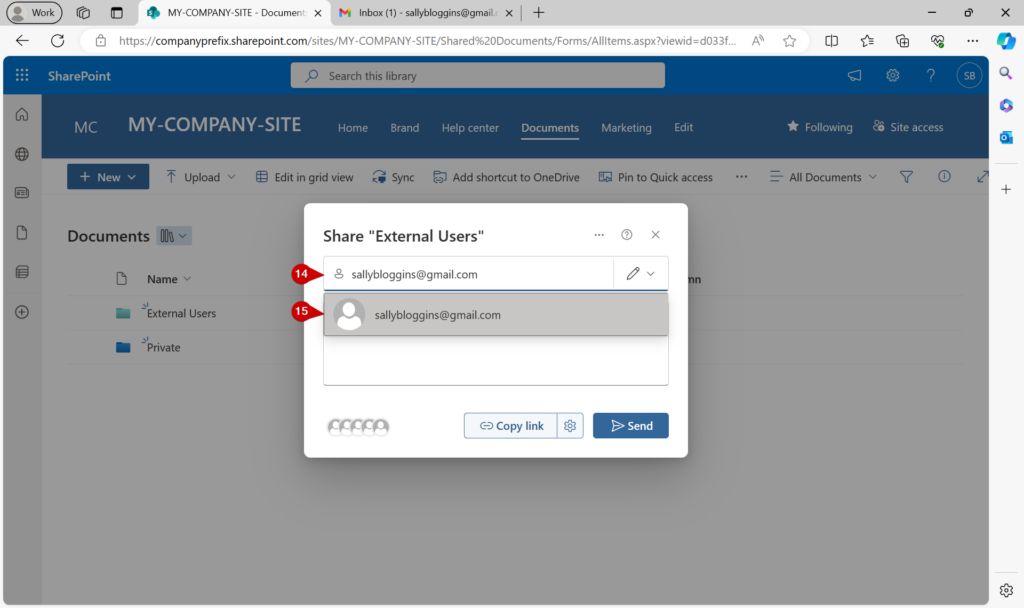
This article explains how to share a link with an external user to your company’s SharePoint.
Cybersecurity Predictions for 2024

As 2024 unfolds, staying ahead in cybersecurity means prepping for AI’s dual role, looming quantum threats, rising hacktivism, persistent ransomware, and influential cyber insurance. It’s crucial to adopt a proactive, comprehensive cybersecurity strategy with regular assessments to navigate these challenges.
Workspaces, a VPN & More – Learn the Newest Microsoft Edge Features

Microsoft Edge introduces Workspaces for customized, persistent browsing environments, aiding task management and productivity. New features include form autofill, Web Capture, AI tools via Copilot, and Read Aloud for multitasking. Microsoft ensures continuous browser updates to enhance user experience.
How to set Automatic Replies in Outlook on the web
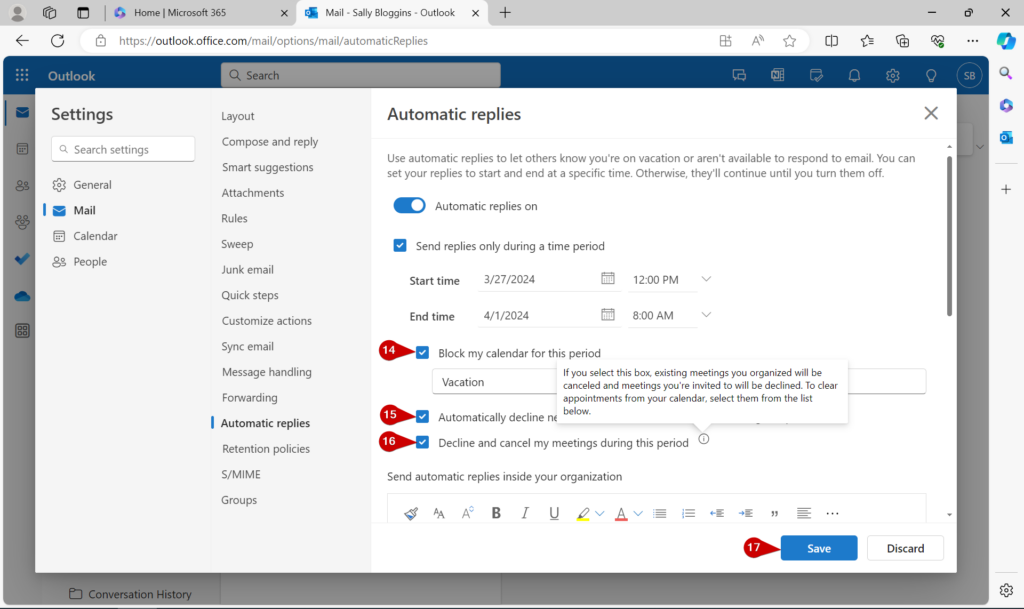
This article explains how to set your Out of Office reply if you are using Microsoft Outlook on the web.
How to set Automatic Replies in Outlook (new)
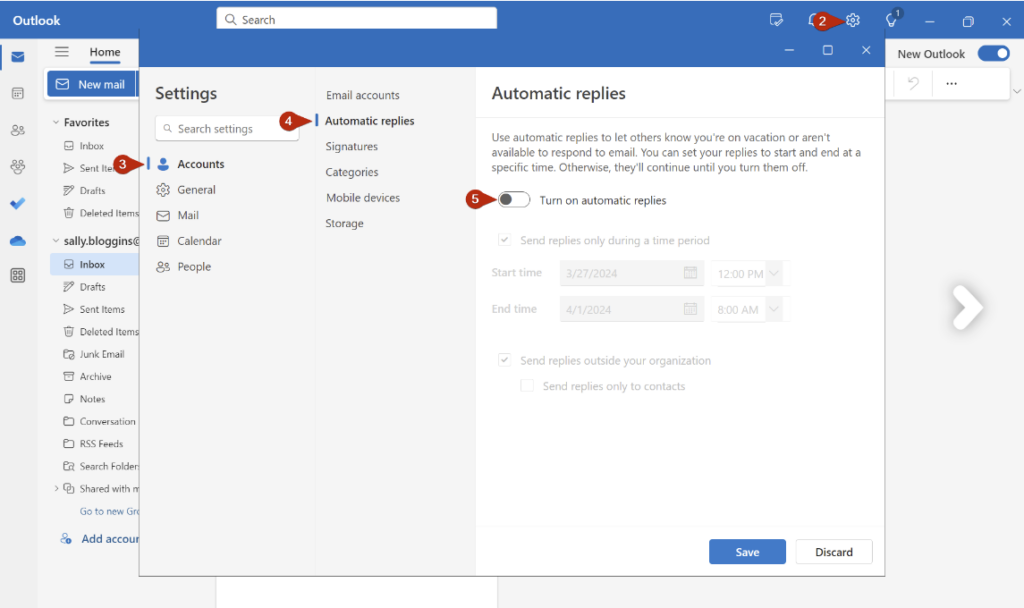
This article explains how to set your Out of Office reply if you are using Microsoft Outlook (new).
How to set Automatic Replies in Outlook (Desktop)
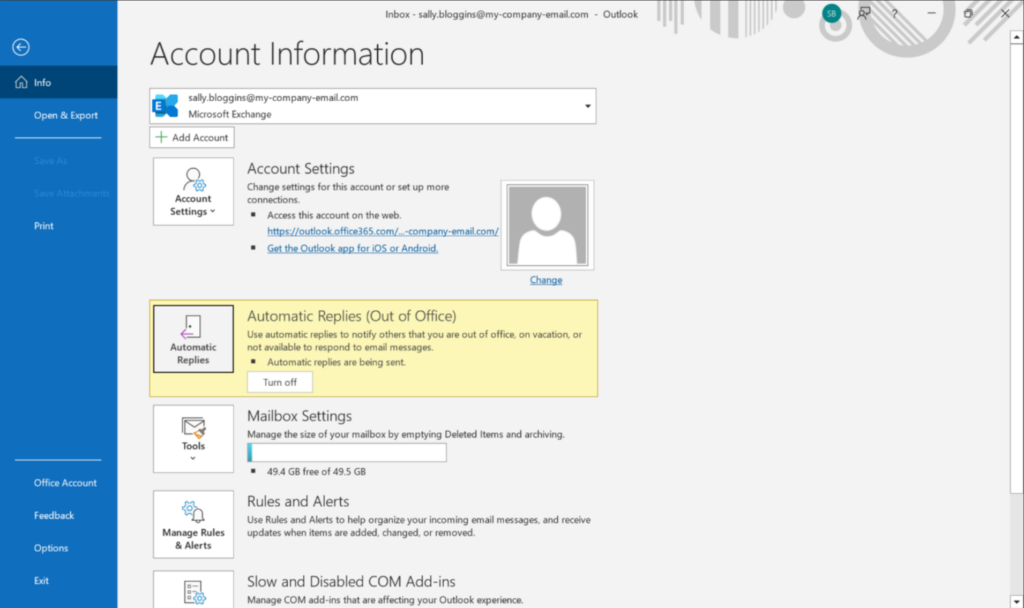
This article explains how to set your Out of Office reply in the desktop version of Microsoft Outlook.
These 7 AI Trends Are Sweeping the Cybersecurity Realm

Relentless digital innovation has defined the last few years. The symbiotic relationship between AI and cybersecurity has become pivotal especially when it comes to safeguarding sensitive information and digital assets. As cyber threats evolve in complexity, AI has emerged as a formidable ally. It empowers organizations with advanced tools and techniques. Helping them to stay […]
How to set Automatic Replies on a Shared Mailbox
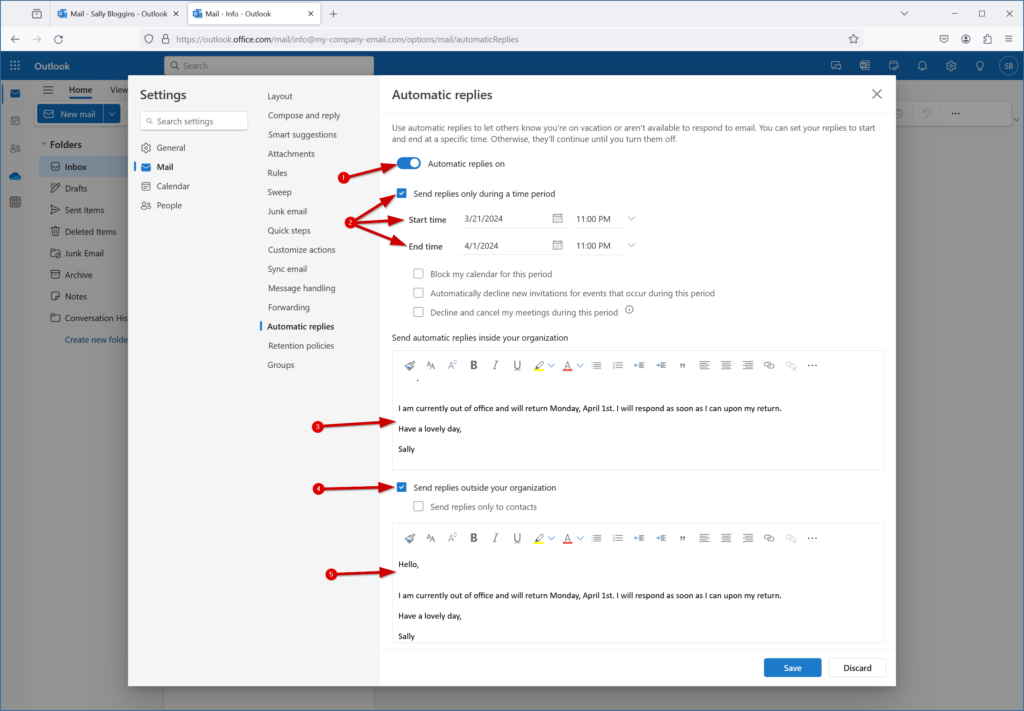
This article explains how to set an automatic reply for a Shared Mailbox.
Knowledge
Knowledge Base Helpful articles and answers to frequently asked questions. Ask us anything! Questions? Comments? Send us a message about this article, or anything else on your mind!
Online Security: The Dangers of Browser Extensions

Browser extensions have become as common as mobile apps. People tend to download many and use few. There are over 176,000 browser extensions available on Google Chrome alone. These extensions offer users extra functionalities and customization options. While browser extensions enhance the browsing experience, they also pose a danger which can mean significant risks to […]
How Small Businesses Are Unlocking Growth With Generative AI

Staying ahead in business often means embracing cutting-edge technologies. New tools can unlock new avenues for growth especially for small businesses. SMBs are often looking for affordable ways to gain a competitive advantage. One such transformative force is Generative Artificial Intelligence (GenAI). This is a technology that goes beyond automation and the AI we used […]
Examples of How a Data Breach Can Cost Your Business for Years

In the digital age, data is the lifeblood of businesses. It fuels operations, decision-making, and customer interactions. But there is a dark underbelly of this data-centric landscape. It’s the persistent threat of data breaches. The repercussions of a data breach extend far beyond the immediate aftermath. They often haunt businesses for years. Only 51% of […]
Demystifying web accessibility: insights and best practices for your website

Over two thirds of adults with disabilities use computers and smartphones, making web accessibility crucial. Organizations must create inclusive websites, starting with understanding impairments ranging from cognitive to motoric. Adopt principles like perceivable content, operable navigation, assistive technology integration, and regular accessibility audits to ensure a frictionless experience for all, enhancing legal compliance, reach, and sales.
Blog
Are Your Smart Home Devices Spying On You?

The integration of smart home devices has become synonymous with modern living. They offer convenience, efficiency, and connectivity at our fingertips. But a recent study has raised concerns about the darker side of these smart gadgets. It suggests that our beloved smart home devices may be spying on us. It’s natural these days to invite […]
5 Ways to Leverage Microsoft 365’s New AI Innovations
Microsoft 365 has a powerful suite of cloud-based productivity tools. They can help you work smarter and faster. Microsoft has consistently been at the forefront of innovation. M365 was one of the very first all-in-one cloud tools, introduced as Office 365 in 2013. Now, Microsoft and its business tools are at the leading edge of […]
Knowledge Base (Tawk Version)
Ransomware Canaries
Ransomware Canaries If you’re a computer user that’s found a strange-looking file on your system guiding you to this page, you’re in the right place! The file you found that led you here is called a ransomware canary. It’s created by a service called Huntress that has been installed and is managed for you by […]
Inventory 2 Test
Home
Enterprise Solutions for Small Business Specialists in providing small and medium business with modern, secure technology and services. How we can help you Information Technology is a huge responsibility, and IT’s not in your job description Consult We work with you to identify problem areas, security risks and outdated technology, then propose solutions that work […]
New Company Enrolment Form
Samsung Galaxy Note 9

Samsung Galaxy Note 9
- 128GB
- glass screen protector installed
- includes Spigen bumper case
Quote – Computer
Sign Up
Files
Contact
For more information, complete the form below or call us at (855) 537-2653 "*" indicates required fields Your Name* Name It doesn’t even have to be your real name but we have to call you something, right? Your Phone NumberSupply your phone number if you’d like us to call you back.Your Email Address* We’re happy […]
Accounting
Submit Ticket
Inventory
Services
Managed IT Services We offer services for businesses of all sizes. Explore solutions below to protect and optimize your technology, and more importantly: your information. Endpoint Management Infrastructure Management User Assistance Security and Privacy Cybersecurity Awareness Data Protection Lifecycle Management Vendor Management Compliance Reporting Domain Name Management Website Hosting Dedicated Servers Cloud Storage Design and […]
Shop
My Account
Checkout
Cart
Cart
